crypt SHA vs. vanilla sha256()
When I tried to bypass crypt() function, because it depends on the glibc, I tried to use ordinary sha256() (language doesn't matter) function. It didn't work. It has never worked. Then I stared to dig into glibc source, because I was curious what the cause was. And I couldn't find any documentation....
Crypt converts a string, e.g. a password to hashed format, so the original string cannot be found out easily.
It supports multiple hash functions, but it depends on operating systems. Any current operating system from 2006 supports the most modern hash algorithms as SHA512 or bcrypt. Debian uses SHA512 now instead of the original MD5 for system passwords.
But in addition to vanilla SHA512 or bcrypt it obsfucates the password with multiple passes, stretches and ..
You can read the manual in man crypt. There is a great manual for PHP implementation - http://php.net/manual/en/function.crypt.php.
crypt outputs something like whis
$6$rounds=5000$usesomesillystri$D4IrlXatmP7rx3P3InaxBeoomnAihCKRVQP22JZ6EY47Wc6BkroIuUUBOov1i.S5KPgErtP/EN5mcO.ChWQW21
Separator is $ dollar and it denotes algorithm, stretches (or rounds, optional), salt and hashed password itself.
Vanilla SHA512 function also supports stretches and salt.
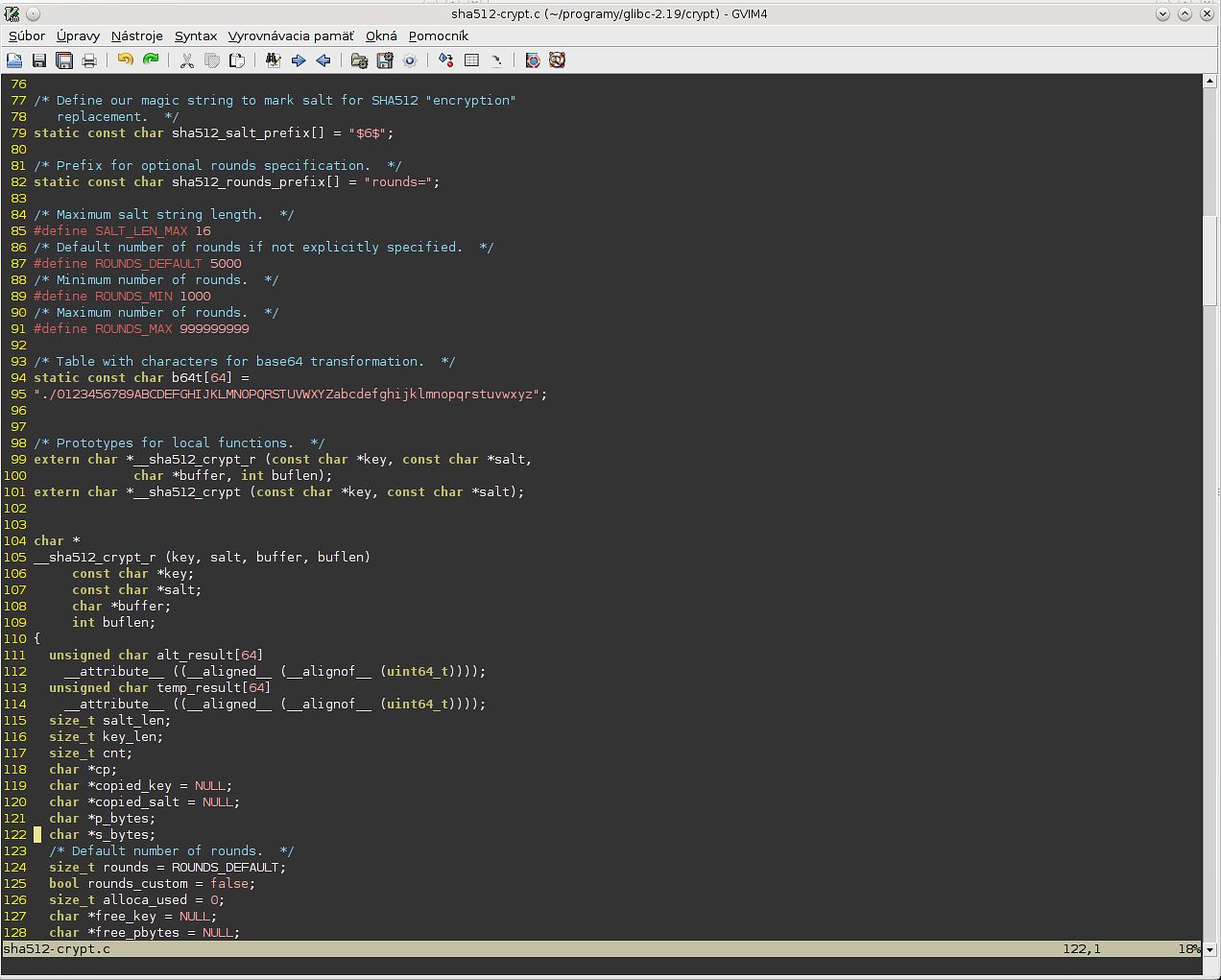
Here you can see default values for salt and password and declaration of __sha512_crypt and __sha512_crypt_r. The second one is thread safe.
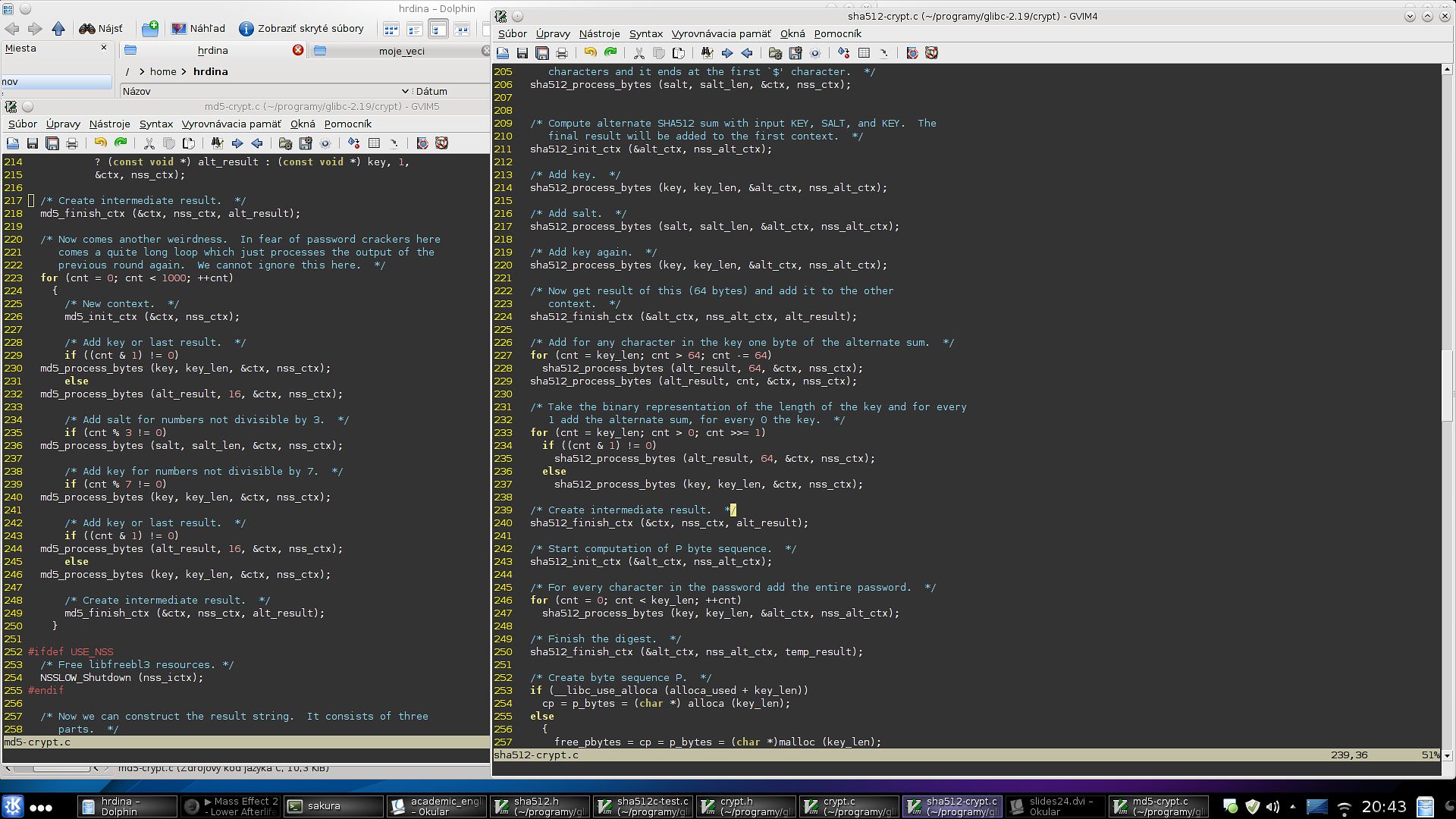
But then it gets uglier. As you can see from the comments - "Compute alternate SHA512 sum with KEY, SALT, KEY". And then this generated string is added to the original (context).
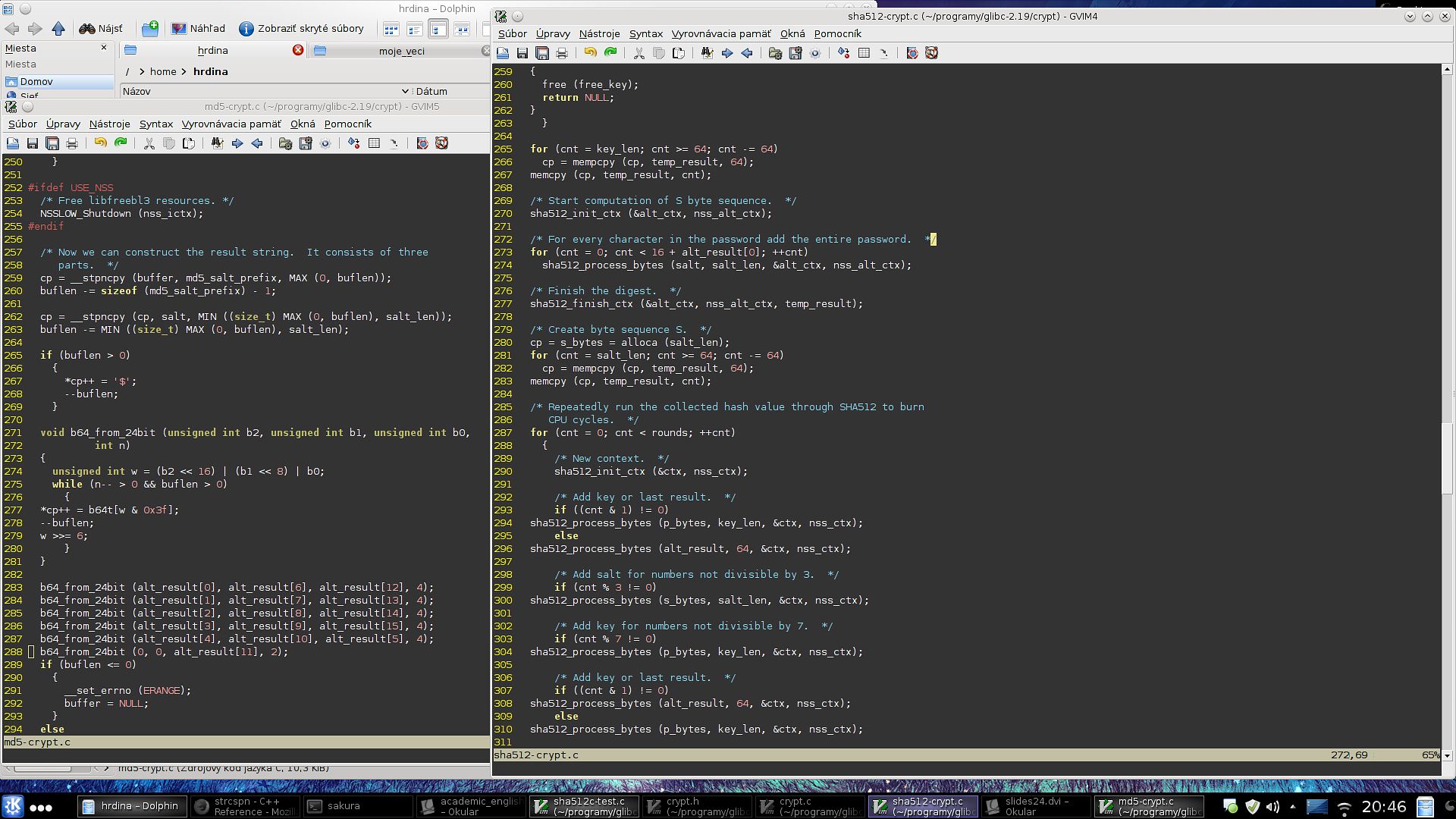
And then "For every character in the password add the entire password" and "add salt for numbers not divisible by 3". crypt() is a magic.
MD5 crypt implementation uses similar techniques.
That's all. You can download glibc to see it yourself. And I hope I'm not wrong and this is not an implementation of SHA or MD5. But I wrote a script which compared passwords from crypt and SHA512 function with the same salt and even various rounds. It had never found the same hash...
Add Comment